Class 7: SQL, SQL Injection, and CSRF
Overview
In this lesson, we will get you familiarized with SQL commands. Then, we will go over how to inject those SQL commands into vulnerable web services.
SQL
Overview
SQL, or Structured Query Language, is used to communicate with a database. A database is a collection of data that is organized into tables. There are other apsects to databases, but most of the time we’ll be dealing with tables only. Here is an example of a table called CUSTOMER:
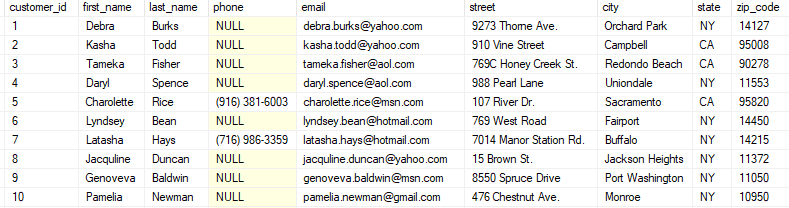
The CUSTOMER table is composed of columns (or fields): customer_id, first_name, last_name, and so on.
Each row is a record in the table. A record is composed of fields (the columns) that contain data about a particular item. For example, the first entry or record in the table has a customer_id of 1, first_name of Debra, last_name of Burks, and so on.
SQL is how we interact with the tables to either insert into or select from them.
Practice SQL commands in sqlite3
Download this database which has most of the scrabble dictionary words. scrabble.sqlite
sudo apt-get install sqlite
To open the database:
sqlite3 scrabble.sqlite
Useful Sqlite commands:
-- Show all tables
.tables
-- Show table struture
PRAGMA table_info(table_name);
Now try running:
select words from racks where rack="AENORST"
Now what command would you run to get all anagrams of “PIRATES” from the db?
Also how would we get all of the anagrams of “PIRATES” of length 4?
Here are some other examples:
-- Select all rows and columns from CUSTOMER table
SELECT * FROM CUSTOMER;
-- Select data in columns 'first_name' and 'last_name'
SELECT first_name, last_name FROM CUSTOMER;
-- Select data in column where certain conditions are true
SELECT email FROM CUSTOMER WHERE first_name = 'Kasha' AND last_name = 'Todd';
SELECT phone from CUSTOMER WHERE last_name = 'Rice' or last_name = 'Hays';
SELECT city FROM CUSTOMER WHERE customer_id > 8;
SELECT zip_code FROM CUSTOMER WHERE first_name LIKE '_e%'; -- _ is a single character; % is zero or more characters
Here is a cheat sheet with more SQL commands and examples.
Challenge: LEAKED_DB
For this challenge, you will need to install Sqlite to interact with the database:
Solve the INTRO_TO_SQL challenge.
SQL Injection
Many login pages submit your username and password (or hash of your password) that you provide as a SQL query that looks something like this:
SELECT * FROM USER WHERE user=your_username AND password=your_password;
and vulnerable login pages will do something stupid like this to get your input:
$user = $_POST['username'];
$pass = $_POST['password'];
$sql = "SELECT * FROM login WHERE User='$user' AND Password='$pass'";
Your input isn’t sanitized at all, and you can mess around with the SQL query in all sorts of ways! Try it out in the challenge below!
Challenge: SQLi
Solve the SQLi challenge.
Blind-SQL Injection
Go over peaCTF challenge
CSRF
Cross-Site Request Forgery (CSRF) is an attack that forces a user’s browser to send HTTP requests that they did not intend to make. The request would be sent to a website that the user is currently logged into, and is meant to trigger an action without the users conset, such as the transferring of money or the changing of a password.
Popular CSRF Attacks
- The Netflix website in 2006 had numerous vulnerabilities to CSRF, which could have allowed an attacker to perform actions such as adding a DVD to the victim’s rental queue, changing the shipping address on the account, or altering the victim’s login credentials to fully compromise the account.
- YouTube was also vulnerable to CSRF in 2008 and this allowed an attacker to perform nearly all actions of any user.
- McAfee was also vulnerable to CSRF and it allowed attackers to change their company system.
Example
Here’s an example of how CSRF can be abused in the GET request that an image makes:
<img src=”http://website.com/changePassword.php/?newPassword=attackerPassword”>
Challenge
Solve the SeaEssAreEph challenge.